When it comes to financial transactions, risks always run high: insufficient business practices or negligence in dealing with banking details, credit cards, or any confidential customer information create avenues for fraud, theft, and unauthorized data exposure. As a consequence, the financial industry is heavily regulated due to the need to ensure maximum data security and promote risk avoidance.
Moreover, Accenture reports that approximately 40% of compliance officers expect to increase investment in their compliance functions. This indicates that financial institutions, including those offering payment processing services, are facing increasingly complex regulatory requirements related to anti-money laundering, data protection, fraud prevention, and other compliance obligations. Therefore, it is crucial to understand standard regulations, recognize the challenges, and know how to implement best practices for effective payment processing compliance management.
Why Following Compliance Standards is Critical for Financial Businesses
Ensuring data security in FinTech applications is paramount. Compliance is one of measures that promotes safeguarding data, and neglecting it can gravely jeopardize a business’s viability. On the other hand, considering payment processing laws from the project’s get-go can help ensure the following criteria.
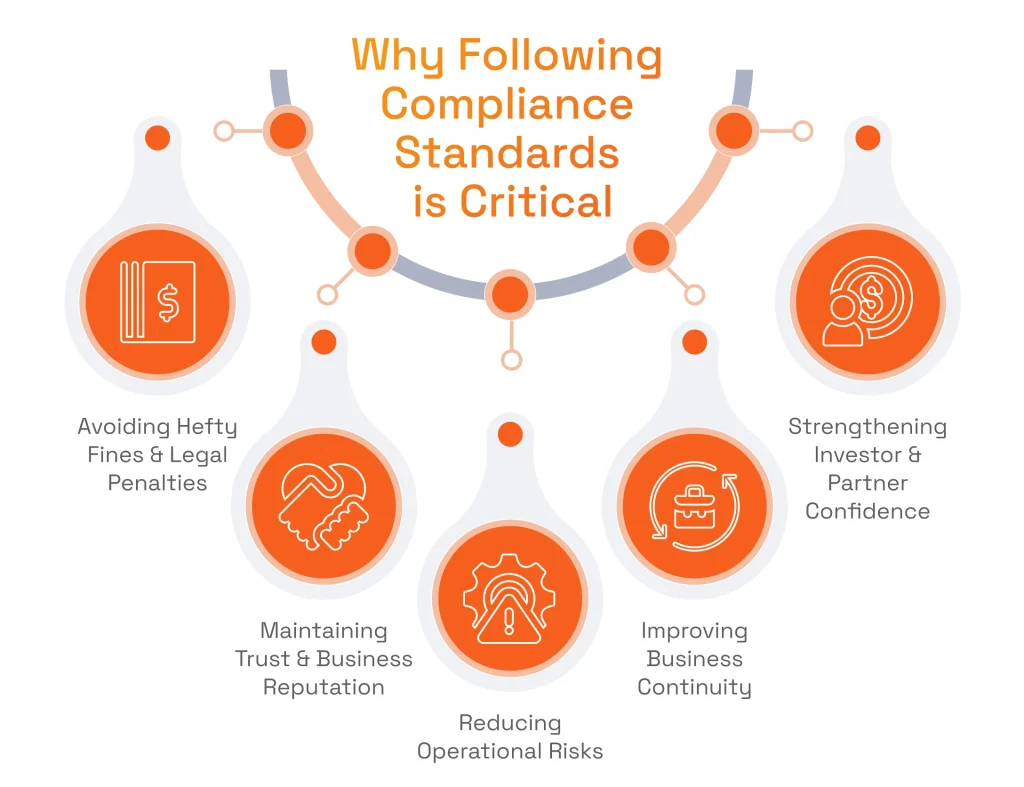
Avoiding Hefty Fines & Legal Penalties
Compliance with payment processing regulations helps businesses dodge costly fines. It ensures that they operate within the legal frameworks set by governing bodies, thereby reducing the risk of non-compliance penalties. Additionally, adhering to payment processing standards minimizes the likelihood of legal action, such as investigations and civil lawsuits, since the company commits to ethical practices and transparent operations.
Maintaining Trust & Business Reputation
Following compliance standards signals to customers and clients that the company is committed to ethical practices and transparency. In this manner, business fosters client loyalty by reassuring them of safe and responsible operations and also enhances the business’s reputation, making it more attractive to potential customers and partners.
Reducing Operational Risks
Businesses that adhere to regulatory guidelines demonstrate that internal processes follow industry-recognized safety measures, reporting, and security benchmarks. All of these are crucial for identifying vulnerabilities before they escalate as in this way companies are proactively managing potential issues such as fraud, data breaches, or process failures, which can cause disruptions to their business.
Improving Business Continuity
The development of robust contingency plans and backup procedures as part of meeting regulatory requirements is vital for sustaining operations during unexpected disruptions. These protocols help ensure that, even in the face of crises, essential functions can continue with minimal downtime.
Strengthening Investor & Partner Confidence
Meeting compliance obligations demonstrates a payment processing company’s stability and dedication to maintaining high standards of governance and risk management. This, in turn, helps build trust among investors and business partners because such a visible commitment to regulatory adherence not only reassures stakeholders about the security of their investments but also creates opportunities for increased funding.
5 Main Payment Processing Compliance Regulations
While there are many laws and frameworks that may apply to payment processing applications depending on region and business model, the following five tend to have the broadest impact and relevance across payment providers.
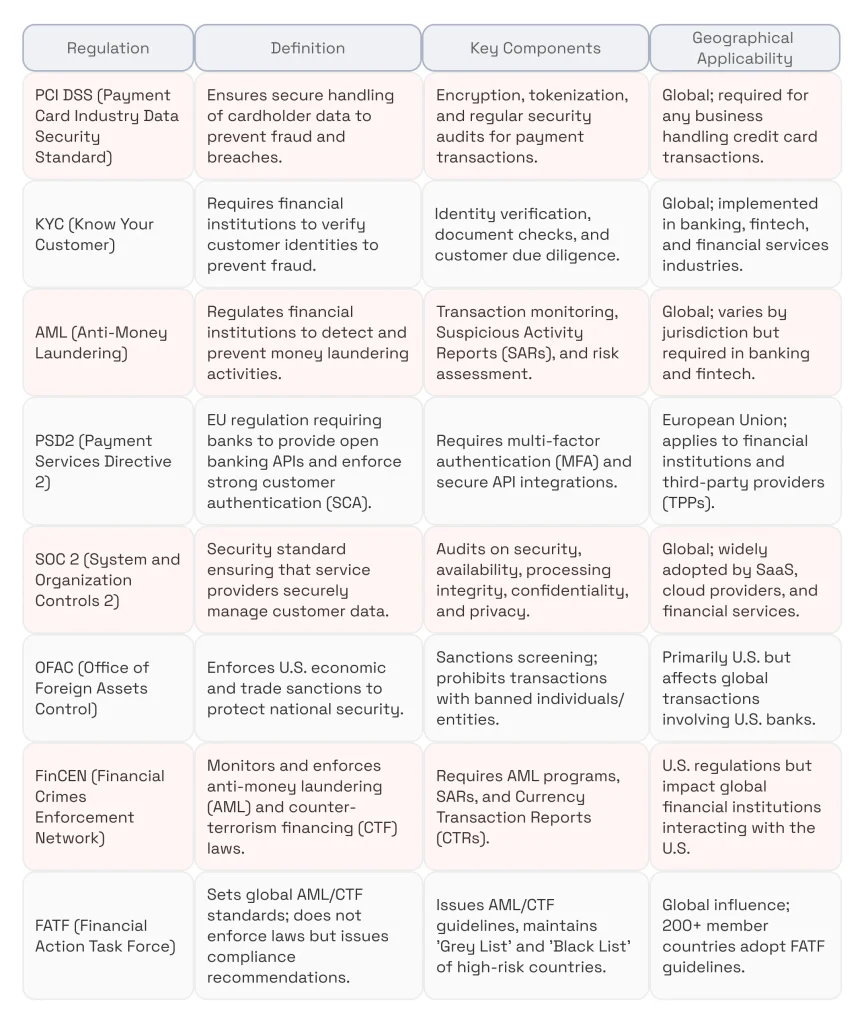
1. Payment Card Data Security Standards (PCI DSS)
Payment Card Data Securities Standards date back to 2004. They came into being as an initiative by 5 major credit card issuers: Mastercard, Visa, JCB, Discover, and American Express.
There are four PCI compliance levels to assess merchant’s adherence to its security standards. These standards are binding upon any business entities that collect, store, transmit, or process cardholder data, which stands for a broad range of business entities, including financial institutions, various merchants, brick-and-mortar retailers, online stores, payment processors, and payment facilitators.
The data that is to be protected in accordance with the PCI DSS compliance requirements is associated with credit, debit, and cash cards and includes credit card numbers, security codes, and card expiration dates.
In addition to precluding cardholder data from being used for fraudulent purposes, PCI DSS compliance is intended to protect payment processing companies against getting exposed to high-risk. It helps prevent data breaches, identity theft, and fraud during the processing and transmitting of card data.
PCI DSS compliance indirectly supports anti-money laundering (AML) efforts. It enhances security by preventing fraud, identity theft, and unauthorized transactions, which are often exploited for money laundering.
The PCI DSS compliance standards are pillared upon 6 main principles:
- Build and maintain a secure network and systems: any credit card transactions are to be handled in a secure network that uses robust but user-friendly firewalls. Any vendor-provided authentication data, like passwords and personal identification numbers are not to be used ongoingly.
- Protect cardholder data: all sensitive payment card information, including the Primary Account Number (PAN), cardholder name, expiration date, and security codes (CVV/CVC), must be secured during both storage and transmission. Any storage of full PANs must be encrypted or tokenized, and security codes must never be stored after authorization.
- Maintain a vulnerability management program: one must implement a vulnerability management program that protects the systems that hold cardholder data against hacking attempts (like, for example, those associated with the use of malware and spyware), as well as eradicate any vulnerabilities that malicious actors can potentially exploit to alter or steal cardholder data. The systems that hold cardholder data must also be free of bugs. These systems are to be updated and patched on a regular basis.
- Implement strong access control measures: access to the computer systems that hold cardholder data is to be restricted, while all the users of such systems are to be assigned a unique ID name or number that must be kept confidential at all times. It is prohibited to use vendor-supplied security parameters, including default passwords, under any circumstances. All system defaults must be changed before deployment to prevent unauthorized access. In addition to electronic safeguards, a compliant business must also protect cardholder data physically, particularly at Points-of-Sale and data storage locations. Businesses should implement access controls, secure storage solutions, and proper disposal methods, such as rendering data unreadable before disposal. While shredding may be used for printed records, PCI DSS compliance does not explicitly require it.
- Regularly monitor and test networks: businesses that work with cardholder data are to monitor and test their networks to make sure that the means that ensure the security of the cardholder data they hold function optimally. For example, all the antimalware and antispyware programs that a business has installed must always be updated to their latest versions.
- Maintain an information security policy: it is necessary to introduce a detailed information security policy that explains the responsibilities of all the process actors involved.
Based on the annual volume of transactions, the PCI DSS standards have 4 validation levels.
If a business fails to comply with these credit card processing laws, the acquiring bank or card network may impose penalties, which can include fines, increased transaction fees, or even termination of payment processing privileges. For severe non-compliance, such penalties can reach millions of dollars. Besides, they can include recurrent monthly fines to be paid by the business entity in breach of the PCI DSS compliance requirements until this business entity becomes fully PCI DSS-compliant.
Quite often, compliance with PCI DSS becomes part of companies’ contractual obligations. In one of our recent articles, we shared a PCI DSS compliance checklist. You are welcome to make sure your company meets the necessary requirements accurately.
2. Know Your Customer (KYC) and Anti-Money Laundering (AML) Regulations
AML and KYC are crucial payment industry regulations businesses must comply with to prevent financial crimes, avoid legal penalties, and maintain trust with customers and financial institutions. Failing to adhere to AML and KYC can mean strict penalties or even business shutdowns imposed by such regulators as FINCEN (US), FCA (UK), and the EU AML Authority.
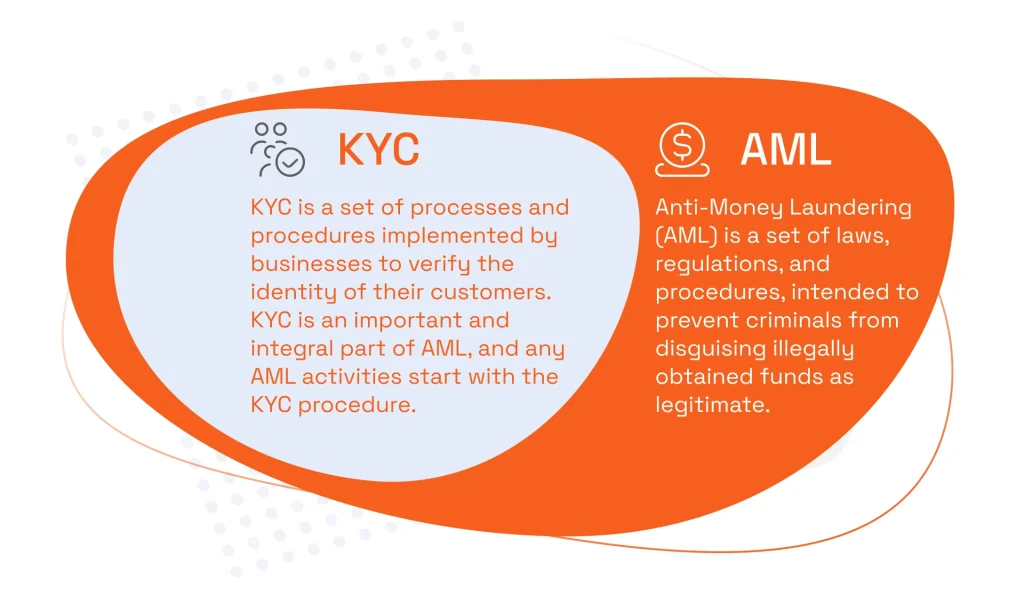
KYC
Implementing KYC standards in Finance is one of the key and most demanding processes banks and Fintechs must complete to achieve the required regulatory compliance.
Often used in conjunction with one another, the terms KYC and AML do not mean exactly the same. In fact, KYC is an important and integral part of AML, and any AML activities start with the KYC procedure.
The KYC regulations outline and mandate the steps and procedures that are to be taken by banks and companies to verify customer identities, assess the legitimacy of their financial activities, and evaluate potential money laundering risks. These procedures help institutions determine the level of due diligence required and ensure payments compliance with AML regulations.
The KYC regulations consist of several components:
1. Implementing a Customer Identification Program (CIP)
As part of KYC, the customer identification program is pivotal in assessing the risks posed by a customer. It focuses on reliably verifying the customer’s identity by cross-checking customer information against various trustworthy sources. In the US, the CIP is part of the Patriot Act that is intended to counter not only money laundering, but also corruption and terrorism funding.
The minimum requirement the CIP puts forward is to check the following details of the customer:
- Name
- Date of Birth
- Address
- ID Number
The types of checks performed can include both document checks and checks against public and other databases.
The CIP or procedure for businesses uses a list of parameters other than that used for individuals. Those may include identifying beneficial owners, verifying corporate structures, and assessing the legitimacy of business activities.
2. Performing Customer Due Diligence
In accordance with the risk a customer may pose regarding money laundering or fraud, there are three levels or types of due diligence performed as part of the CIP:
- Simplified Due Diligence (SDD)
- Customer Due Diligence (CDD)
- Enhanced Due Diligence (EDD)
The due diligence process includes several steps, with varying levels of scrutiny depending on the risk category:
- Customer identification and verification (CIP).
- Beneficial owner identification and verification (for legal entities).
- Assessing the nature of the customer relationship and risk level (CDD and EDD).
- Ongoing monitoring of transactions to detect suspicious activity (part of AML compliance).
Let’s now look at the types of due diligence that make up the CIP in more detail:
- Simplified Due Diligence (SDD): the most simple type of due diligence that is applicable in those cases, when the risks a customer poses are considered to be low. Correspondingly, while having all the basic features of the standard customer due diligence, SDD has a lower verification threshold. Because of this, while performing SDD, business organizations are entitled to adjust such parameters as the quantity of the information used for verification purposes, the types of such information, the frequency of transaction monitoring, and others.
- Customer Due Diligence (CDD): the baseline or standard due diligence procedure that financial institutions and other relevant business organizations are obliged to complete. This involves collecting personal or business information, verifying the data, and screening customers against sanctions lists, watchlists, and financial crime databases.
- Extended Due Diligence (EDD): the type of due diligence that is applied in the case of high-risk customers. To achieve a more thorough and comprehensive customer verification for risky customers, EDD can include various additional checks, like, for example, checks against sanction lists and watchlists, real-time asset tracking, and adverse media screening.
3. Ongoing Monitoring
Ongoing monitoring aims to detect signs of customers’ suspicious financial activity. Financial institutions track transaction patterns, cross-border payments, account balances, and external factors (such as adverse media) to flag potential money laundering or fraud.
Examples of the signs of unusual or suspicious activity that financial institutions can be on the lookout for during ongoing monitoring include tangible spikes in customer activities, untypical cross-border transactions, and newly appeared adverse media mentions.
The set of the control parameter values for ongoing monitoring is determined in accordance with the customer’s risk profile.
AML
Anti-Money Laundering (AML) is a set of laws, regulations, and procedures, intended to prevent criminals from disguising illegally obtained funds as legitimate. In the financial services industry, all market players are obliged to stringently uphold all the existing AML regulations.
The backbone of AML compliance is the AML program that relevant businesses must introduce. This program must include:
- Designating an AML compliance officer responsible for overseeing regulatory procedures, ensuring adherence to AML laws, filing suspicious activity reports, and updating compliance policies as needed.
- Developing the internal compliance policies and actionable protocols that state how the various suspicious activities are to be responded to.
- Implementing an AML risk assessment framework that evaluates clients, business relationships, services, products, geographies, and other risk factors to detect potential money laundering threats.
- Training the company’s employees and personnel.
- Conducting an independent AML compliance review, audit, or regulatory examination to assess the effectiveness of AML policies and procedures.
Andrii Semitkin
Delivery Director
“It’s best to put compliance – the part and parcel of what’s required in the Fintech niche – high on your list of priorities yet well prior to the kick-off of your software development effort. There are too many important details to be taken into account and you should discuss them with your IT provider early enough in the project development cycle.”
3. PSD2
The Revised Payment Services Directive (PSD2) is a regulatory framework that imposes payment processing standards to ensure the security of payments within the EU. For this purpose, the framework focuses on such aspects as consumer rights, access of third parties to consumers’ accounts, and the security of eCommerce.
For example, with regards to consumer rights, PSD2 mandates that payment service providers establish effective complaint-handling procedures for consumers and requires EU Member States to designate authorities responsible for addressing complaints regarding potential PSD2 violations.
Security-wise, PSD2 requires consumers to perform strong customer authentication (SCA) for electronic payments, which involves at least two of the following: knowledge (e.g., password or PIN), possession (e.g., mobile device or token), and inherence (e.g., fingerprint or facial recognition). SCA is required during payment transactions, not just at login. Third-party providers (TPPs), such as payment processors and account information service providers, can access customer account data only with the account holder’s consent, using secure APIs provided by banks. These TPPs must be licensed and use PSD2-compliant certificates for authentication.
When it comes to travel, ticketing, and food delivery transactions, PSD2 prohibits merchants from imposing surcharges on consumer debit and credit card payments. However, the ban applies specifically to card payments regulated under PSD2 and does not cover all payment methods.
4. SOC2
The System and Organization Controls (SOC2) framework was introduced by the American Institute of Certified Public Accountants (AICPA) with a view to regulating the way technology and cloud providers handle customer data.
To minimize risks and reduce the odds of data exposure, the framework provides a set of criteria, as well as some auditing practices that help ensure that both the internal controls of a company and the way they utilize their various compliant systems are up to par.
SOC2 focuses on the following 5 criteria:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
In evaluating the internal controls of a company, the SOC 2 framework uses two types of reports:
- SOC 2 Type 1: a snapshot of the target controls and the extent to which they correspond with the outlined criteria at a given point in time. The report considers the design of the controls the company has in place.
- SOC2 Type 2: a snapshot of the target controls over a specified span of time. The minimum time period a SOC 2 Type 2 report can cover is typically 3 months, though many organizations opt for a period between 6 to 12 months.
5. OFAC, FinCEN, and FATF
In comparison to compliance payment industry regulations mentioned above, that focus on data security, payment regulations, and financial crime prevention at the business and consumer levels, OFAC, FinCEN, and FATF primarily focus on broader financial crime enforcement, sanctions compliance, and global AML policy development.
OFAC
The Office of Foreign Assets Control (OFAC) is a department within the US Department of the Treasury responsible for imposing economic and trade sanctions based on US foreign policy and national security goals. These sanctions can be levied against entities or regimes engaged in illegal activities.
Non-compliance with OFAC can mean civil monetary penalties that can result in large civil fines, regulatory enforcement actions, such as cease-and-desist orders and loss of charter or licenses, or even criminal penalties leading to fines and potential imprisonment for individuals responsible.
Financial institutions and companies are expected to implement robust systems that continuously screen their customer base and transactions against OFAC violations. In practice, this entails several key components:
- Regular Updates
- Risk-Based Analysis
- Clear Escalation Procedures
- Clear Recordkeeping
- Employee Training
OFAC regulations often operate under a “strict liability” framework. This means that an organization can be held liable even if a violation was unintentional.
FinCEN
When it comes to collecting and analyzing information on potential money laundering, terrorist financing, and other financial crimes, the Financial Crimes Enforcement Network (FinCEN) comes into play. Just like OFAC, it is a bureau within the U.S. Department of the Treasury. FinCEN implements and enforces compliance with the Bank Secrecy Act (BSA), which sets recordkeeping and reporting requirements for financial institutions.
Suspicious activity reports (SARs) and currency transaction reports (CTRs) are foundational elements in FinCEN’s regulatory framework with crucial functions:
- SARs must be filed for any transaction that suggests money laundering, terrorist financing, or other suspicious behavior.
- CTRs must be submitted for cash transactions over a certain threshold (generally $10,000).
Failure to follow FinCEN regulations can result in large civil fines (in case of not filing SARs or CTRs properly), cease-and-desist orders, loss of charter or licenses, and enhanced regulatory scrutiny (for businesses), or imprisonment (for individuals in charge of a non-compliant business).
FATF
In the case of setting international standards and monitoring global compliance, the Financial Action Task Force (FATF) plays an important role. This intergovernmental organization was created to combat money laundering, terrorist financing, and other financial threats in the international financial system. The FATF recommendations consist of 40 guidelines, including the following:
- Criminalizing money laundering and terrorist financing.
- Implementing a risk-based approach.
- Ensuring thorough customer due diligence and identifying beneficial ownership.
- Reporting suspicious transactions and record-keeping.
- Encouraging international cooperation.
- Regulating financial institutions and certain businesses.
- Ensuring transparency on legal ownership structures.
- Empowering supervisory authorities with proper measures.
- Protecting customer confidentiality.
When companies neglect FATF regulations, the organization does not directly impose fines or legal penalties. Instead, it can “gray-list” or “blacklist” jurisdictions that have significant deficiencies in their AML/CFT regimes. This, in turn, can create significant economic repercussions.
The Best Practices in Ensuring Payment Processing Compliance
Although the different payment compliance regulations vary in their specific purpose and tool set, there are several universal best practices that can help achieve their goals.
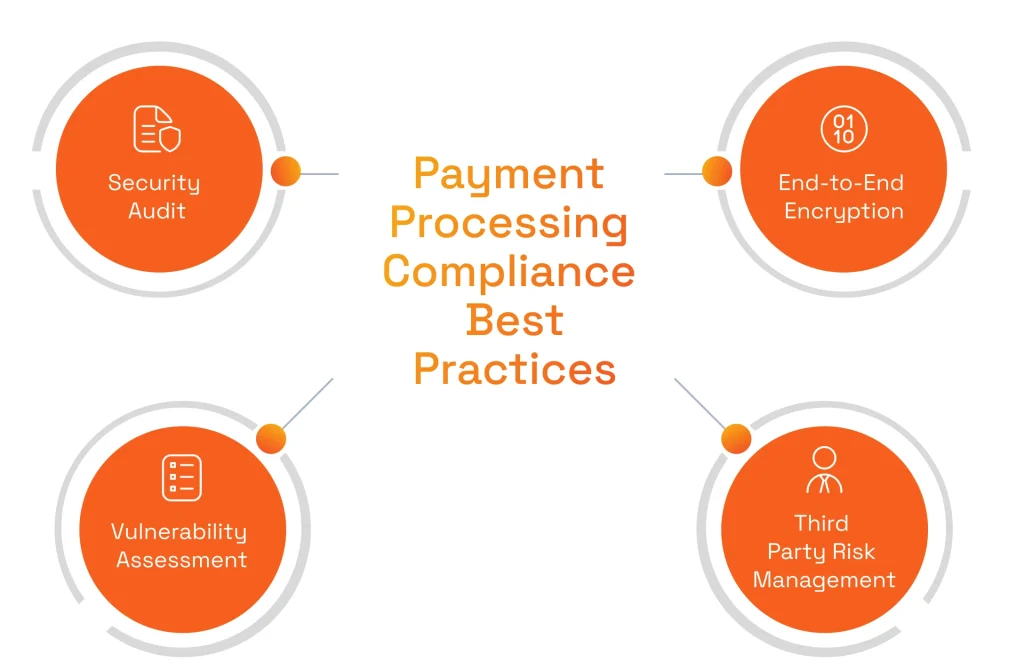
End-to-End Encryption
Presently, implementing data security in financial applications is unthinkable without data encryption. Correspondingly, end-to-end data encryption is an absolute must-have for achieving the necessary regulatory compliance in this realm.
When it comes to protecting customer data, it is imperative that such data be protected when both at rest and in transit. To protect data at rest, one must use one of the several strong encryption algorithms. The more widespread of such algorithms include AES256, Blowfish, Twofish, and RSA. Please note that it is always advisable to use longer encryption keys, and you should consult your IT partner about which key length can be considered sufficiently secure for the strong encryption algorithm of your choice – this length can vary from algorithm to algorithm.
As far as data in transit is concerned, it must be protected using either the Secure Socket Layer (SSL) certificate or Transport Level Security (TLS) encryption. Although SSL is still widely used, TLS is a more secure, and, correspondingly, more preferable option. It uses enhanced encryption algorithms, encrypted alert messages (in SSL, the alert messages are unencrypted), and a more advanced message authentication algorithm. The latter allows protecting the data being transported from tampering by malicious actors.
Security Audits and Vulnerabilities Assessments
To ensure payments compliance, it is essential that one conducts regular PCI DSS and other compliance audits. These audits must be both internal and external, i.e. involve an accredited third party.
Discovering and assessing vulnerabilities in a company ecosystem is an effort-intensive process that one must conduct on an ongoing basis. For better results, it makes sense to employ several approaches.
One of such approaches is using well-scoped penetration testing (black-box, white-box, or gray-box) applied to both the systems and networks used. Under this approach, your in-house experts or those of your IT partner simulate real-world hacking attacks on your IT infrastructure with the goal to detect any possible vulnerabilities.
Another approach that can prove very effective is implementing a company-wide policy that would encourage both your IT and non-IT employees to practice a proactive attitude and raise a flag whenever something within their area of responsibility seems to be not up to par in terms of security.
Vendor and 3d-Party Risk Management
Vendor other third-party relationships may pose significant risks too. These include cybersecurity, operational, and other risks. This is especially true when partnering with firms that provide payment gateway integration services, as their solutions must align with your security and payment gateways regulations to prevent any regulatory breaches.
To deal with such risks whether during web or mobile payment gateway integration, you should first clearly describe the nature of your future relationship with a vendor or some other third party. Once this is done, you should apply due diligence in accordance with their profile. Finally, you should request your partner-to-be to fill in any gaps that you have found.
Also, it’s advisable to manage and mitigate third party risks with the help of service-level agreements (SLA). In these agreements, you should clearly indicate the ways in which any possible security and data privacy risks are to be taken care of by the third party you are dealing with.
Payment Processing Compliance Challenges
In addition to the need to fully encompass the various demands of the compliance regulatory frameworks and deal with the various numerous risks, payment processing companies also have to cope with several other significant challenges.
Being aware of these challenges not only helps tackle them in time, but also allows you to do so with a systematic approach, beforehand, and in a comprehensive manner.
So, what are these challenges?
Evolving Regulatory Landscape
Over recent years, the regulatory landscape around payment processing seems to have been constantly undergoing a massive amount of change. Such changes are virtually guaranteed to continue far into the future, as regulators are trying to keep pace with the fallout of several factors that are constantly evolving at a fast speed.
Such factors include the emergence of new payment methods, the growing role of payment facilitators on the payments market, the ever-evolving cyber threats that are also growing in number, the ever increasing amount of fraud, and others. Examples of the regulations that have come into being in response to these developments include GDPR that took effect in on May 25, 2018, the Strong Customer Authentication (SCA) requirement of PSD2 that came into force on September 14, 2019, and the AMLD 5 directive that was released on June 19, 2018.
We performed payment gateway development services for many financial apps as well as integration of payment processing functionality and recognized the significance of regulatory frameworks for such apps.
To make sure we are aware of all payment gateway compliance requirements when building a payment gateway, we proactively monitor regulatory changes, implement robust yet flexible security measures, and strike a balance between security requirements and a seamless user experience. Plus, we also dedicate resources to:
- Integrate advanced encryption, tokenization, and AI-driven fraud detection to minimize threats.
- Collaborate with legal experts and regulators to stay ahead of impending compliance changes.
- Adopt multi-factor authentication methods that maintain robust security while ensuring minimal user friction.
Conflicting Security and User Experience
The security safeguards payment processing companies need to put in place often tend to come into conflict with the need to provide seamless user experience (UX). Because of this, it is essential for payment processors to carefully consider the different existing security-related options and choose those of them that allow sufficient user-friendliness without compromise on security.
Wonder how to start a payment processing company? Follow our getting-started guide!
While working on payment processing applications, we see that implementing robust security measures with a seamless UX can be conflicting. For example, using PSD2-compliant security tokens as a security factor in MFA can ensure a sufficient level of security. At the same time, security tokens cannot be considered as a user-friendly means of ensuring security. For this reason, we prefer adopting multi-factor authentication approaches that incorporate user-friendly biometric options or frictionless methods where possible.
In some cases, it is better to use a more “seamless” security factor, like, for instance, iris recognition or advanced face recognition. The key is to continually assess the impact of security features on the user journey and refine them. For that, we usually perform the following:
- Comparing traditional security tokens with biometric methods for usability and security strength.
- Integrating advanced face/iris recognition solutions that meet PSD2 requirements while improving user convenience.
- Continuously testing authentication workflows to ensure minimal friction and maintain a high level of security.
- Dynamically adjusting authentication levels based on transaction risk profiles to minimize customer disruption.
Adopting Artificial Intelligence
Implementing AI in payment processing applications has the potential to significantly improve security. In fact, one of the key payment processing industry trends is the adoption of AI-driven risk analysis and real-time fraud detection, both of which require robust data governance to remain compliant. Alas, the downside is there too.
At the same time, regulators require strict adherence to privacy and consumer protection laws when implementing AI in FinTech. This puts a heavy burden on payment processors to handle sensitive data responsibly. AI-assisted regulatory compliance can help meet these requirements by automating many of the manual, error-prone tasks associated with risk assessments and reporting. However, this approach also introduces challenges.
For example, during one of our projects we were tasked with custom AI solutions development and needed to make AI models used in payment processing apps transparent so that every decision was clear and fair. At the same time, we were required to protect the data used by these models. To navigate this complexity, we used:
- Regulatory-aligned AI frameworks that are pre-configured to align with key payment processor regulations.
- Explainable AI solutions that are designed with interpretability in mind, ensuring that audit trails and decision logic is transparent.
- Robust security measures such as data tokenization, encrypted data storage, and real-time threat detection tailored for AI-driven environments.
- Data analytics that can validate model performance by revealing biases or anomalies that might affect compliance, security, and fairness.
Interested to know how financial companies arrive at critical decisions?
Learn about data analytics in finance.
Why Partnering with Reliable Vendor Is Critical to Develop Compliant Financial Software
Regulatory requirements in the finance industry get updated frequently, and maintaining impeccable security standards is non-negotiable. By partnering with the best FinTech development companies, the businesses can be sure that these standards are prioritized. Moreover, with a seasoned technical vendor, businesses can get the possibility of:
- Ensuring Compliance-Driven UX & Customer Trust: A FinTech vendor designs software with regulations in mind from the start to provide both user-friendly and fully compliant apps that grant users peace of mind over security of their data.
- Secure Architecture Engineering & Data Protection: An expert partner knows how to implement best-in-class security protocols, such as encryption and tokenization, to ensure compliance for payment service providers and prevent costly data breaches and protect sensitive financial data.
- Building Scalable & Future-Proof Financial Software: A tech company understands the market nuances and develops systems with in-built payment compliance that can adapt to future market and regulatory demands.
- Incorporating Ethical AI: A reliable FinTech vendor offers AI consulting to ensure that advanced analytics and machine learning solutions are designed responsibly and eliminate bias.
Consider SPD Technology as Your Compliance & Security-First Software Developer
Our team is dedicated to helping businesses navigate the intricacies of modern FinTech regulations. We enhance payment processing software thanks to incorporating payment security standards, prioritizing fraud detection software development, and implementing AI for software data protection. When collaborating with us, our clients also get:
- Advantages of strategic technology consulting: We guide businesses from the initial concept to final deployment to make sure that the software aligns with both regulatory requirements and business objectives. In this way, we can mitigate compliance risks early and deliver the app up to market demands.
- Expertise in building PCI DSS-compliant payment systems: With proven experience in designing and deploying secure, PCI DSS-compliant infrastructure, our team implements robust encryption, tokenization, and fraud-prevention measures to protect payment data.
- AI-powered fraud detection and AML compliance solutions: Our background on using machine learning in banking, investment, and asset management allows us to set up automated AML checks and due diligence processes for improving precision in minimizing regulatory risks.
- Experience with global payment regulations (PSD2, GDPR, OFAC, etc.): Our professional team has a compliance-first mindset and monitors and adapts solutions to meet new standards when they appear.
- Seamless integration of compliance into FinTech platforms: Instead of adding compliance as an afterthought, we embed regulatory safeguards into the architecture of FinTech solutions from the ground up to make payment processing platforms resilient.
SPD Technology’s Success Stories
We have delivered several projects for FinTech and are happy to share our expertise in implementing payment processing regulatory compliance rules.
Streamlining Merchant Onboarding for BlackHawk Network
BlackHawk Network (BHN) sought to revamp its process for onboarding new businesses into their Original Content Program.
Business Challenge
The client struggled with the manual approach of collecting information and creating leads in Salesforce while also following OFAC and EIN/SSN regulatory requirements. This created the need for a self-service platform capable of seamlessly integrating various compliance checks and data migration tasks.
SPD Technology’s Approach
We developed Aggregated Merchant Portal (AMP) and Admin Portal from scratch to automate registration workflows, integrate with Salesforce for automated lead creation, support a subscription-based model, and enable POS terminal setup. All was done while allowing for dedicated data migration from legacy platforms and prioritizing OFAC and SSN/EIN check in onboarding processes.
Value Delivered
Upon completion, BHN received a new platform with an accelerated merchant onboarding process that complies with credit card processing regulations. Additionally, the platform’s design provided for:
- Reduced time cut from 7 days to under 24 hours.
- Significant cost reduction by minimizing manual processes.
- Successful migration of 8,000+ existing businesses.
- Seamless integration with Salesforce and internal payment systems.
Building a Real-Time SMB Funding Platform for Business Expansion
Our client, a well-established provider of business funding services, aimed to create a modern SMB lending platform to attract a broader range of merchants and enter new market segments.
Business Challenge
The client’s existing lending business needed an innovative digital solution to provide quick access to working capital, reduce weekend or holiday delays, and diversify its service offerings.
SPD Technology’s Approach
Working closely with the client’s CTO, our team developed an extensive commission calculation system, integrated third-party services for risk assessment and system analysis, and collaborated directly with banking partners to ensure the platform could facilitate real-time financing. We built the platform from scratch with scalability in mind and, thus, helped define and refine the client’s product vision while incorporating features such as customizable commission structures and seamless account linking.
Value Delivered
We delivered a full-fledged funding platform that now enables merchants to register, get verified, and secure funding in a single day. The platform’s new architecture provides enhanced functionality for account integration, payment services, and external data checks for complying with payment processor regulations. As a result, the client successfully entered new market niches, attracted thousands of new SMB customers, and secured plans for business growth.
Elevating Payment Solutions for a B2B FinTech Innovator
Poynt needed to enhance its suite of payment solutions by transitioning to a PayFac (Payment Facilitator) model, integrating multiple third-party processors, and streamlining both merchant onboarding and settlement processes.
Business Challenge
With the need to serve businesses of all sizes, Poynt needed to become a PayFac and aimed to upgrade its billing services, expand digital wallet support, and build a robust UI component for embeddable payments. These goals required a complete overhaul of existing architectures, compliance with multiple certifications, and continuous support.
SPD Technology’s Approach
We began by redesigning the internal settlement service for PayFac transactions and overhauling the subscription system to accommodate new billing models. Our professional team then developed a React-based embeddable UI component, allowing seamless payment collection within merchant checkout pages. Parallel to these improvements and as part of our payment processing app development efforts, we implemented a regression testing framework, a revamped integration module for new processors, and a data synchronization infrastructure to ensure real-time updates between core systems.
Value Delivered
Our efforts in redesigning and reinventing the platform enabled Poynt to become a fully operational payment facilitator in line with compliance for payment service providers. As a direct result, Poynt get:
- Major client acquisition by a global company.
- Expanded payment processor integrations.
- Enhanced service offerings.
Conclusion
Understanding payment compliance meaning is crucial: it’s adhering to the laws, regulations, and industry standards for financial transactions. We’ve made a brief overview of the requirements FinTechs and other businesses must meet for ensuring credit card payment processing compliance and other standard compliance for payment processing.
Prior to embarking on this complex process, you should become well-acquainted with the corresponding regulatory documentation and be prepared to discuss your current business situation and needs with your IT provider and any other parties that may need to be involved. As to the best practices we’ve touched upon, our FinTech development team has nearly two decades of experience in dealing with various FinTech development challenges and would be delighted to tell you more about this topic, just feel free to ask.
FAQ
What is PCI compliance?
PCI DSS compliance is a mandatory compliance framework that regulates the handling (collection, storage, transmission, or processing) of cardholder data by such businesses as financial institutions, various merchants, brick-and-mortar retailers, online stores, payment processors, and payment facilitators.
How to implement PCI DSS compliance?
You should gain an overall understanding of the PCI DSS compliance requirements, become aware of the best practices that can be helpful, find a knowledgeable IT provider with sufficient Fintech development experience, compose a PCI DSS compliance checklist jointly with them, and discuss with them the development options they can offer.


