As we continue to discuss the realm of Fintech, and building custom software solutions for this industry, it’s time to cover one of the most prominent aspects of any financial software – ensuring fintech data security. In our previous articles, we discussed how to build a payment gateway and how much it costs. This time we will focus on PCI DSS compliance requirements, the most important security aspect of any company processing financial information online.
What makes data security and PCI DSS compliance one of the most crucial considerations for fintech companies? According to IBM, the global average cost of a data breach in 2023 was USD 4.45 million. In addition to that, your business may be penalized by up to $100,000 a month for being non-compliant with PCI DSS, so this is critical for organizations dealing with financial transactions.
PCI DSS requirements were designed to better control cardholder data and reduce credit card fraud. The latest version was made available in March 2022. Its changes are quite significant and cover even more possible security risks, compared to the previous versions.
Why Ensuring PCI DSS Compliance Is Important?
Following the PCI compliance checklist is crucial for safeguarding cardholder data, maintaining customer trust, preventing fraud, avoiding financial losses, managing risks, and ensuring the continuity of business operations. Let’s discuss these points in more detail.
Protection of Cardholder Data
The main reason to follow the PCI DSS compliance requirements checklist in the first place, is that the standard is aimed at protecting cardholder data during its processing, transmission, and storage in your organization. It leverages such techniques as encryption and access controls, to help prevent unauthorized access and potential breaches of sensitive payment information.
Customer Trust, Confidence, and Identity Theft Prevention
Your reputation matters since the brand image can make or break an organization. Adhering to PCI DSS compliance, implementing KYC standards in financial services, and other regulatory frameworks designed to enhance security, reduce fraud, and protect sensitive information is a foundational element of an exceptional reputation of your organization. When your customer knows that all payment information is handled at the highest level of security, it builds trust in your company and becomes a great foundation for potential growth.
Following, the PCS DSS checklist, or any other regulatory framework for that matter does not guarantee 100% incident-free operation, however, it is safe to say that it dramatically reduces the risk of fraudulent activities and unauthorized transactions. Security measures like strong access controls and regular monitoring contribute to the detection and prevention of suspicious activities, resulting in a safer environment for your organization.
Avoidance of Data Breach Costs
Along with reducing fraud, following the PCI-DSS compliance checklist can also prevent major financial losses and legal consequences. Data breaches have always been among the top Fintech development challenges. If Statista is to be believed, the average total cost per data breach worldwide in 2023 was an astonishing $4.45 million.
Ongoing Monitoring and Risk Management
PCI DSS encourages continuous monitoring and risk management practices, as regular assessments and monitoring help organizations stay vigilant against emerging threats and vulnerabilities, allowing for timely response and adaptation to changing circumstances.
Global Business Operations, Partnership, and Vendor Requirements
Many global businesses require PCI DSS compliance as a prerequisite for partnerships and collaborations. So, PCI DSS compliance unlocks new potential opportunities for your business, meeting the expectations of partners, vendors, and regulatory bodies.
Efficient Incident Response and Business Continuity Preservation
PCI DSS compliance audit checklist also includes a well-defined incident response plan, that ensures organizations are prepared to address and mitigate security incidents if they actually happen. This plan helps to preserve business continuity and minimize any possible downtime.
Demonstration of Due Diligence
Compliance efforts showcase a commitment of your company to meeting industry standards, reducing risks, and fulfilling its responsibility to safeguard payment card data.
Adaptability to Changing Threat Landscapes
The threat landscape is extremely dynamic, with new risks and vulnerabilities, unfortunately, emerging regularly. PCI DSS compliance encourages organizations to stay adaptable and responsive to changing cybersecurity threats, fostering a proactive approach to security.
Now, let’s take a closer look at the PCI DSS compliance checklist and discuss its most important aspects.
PCI DSS Compliance Requirements
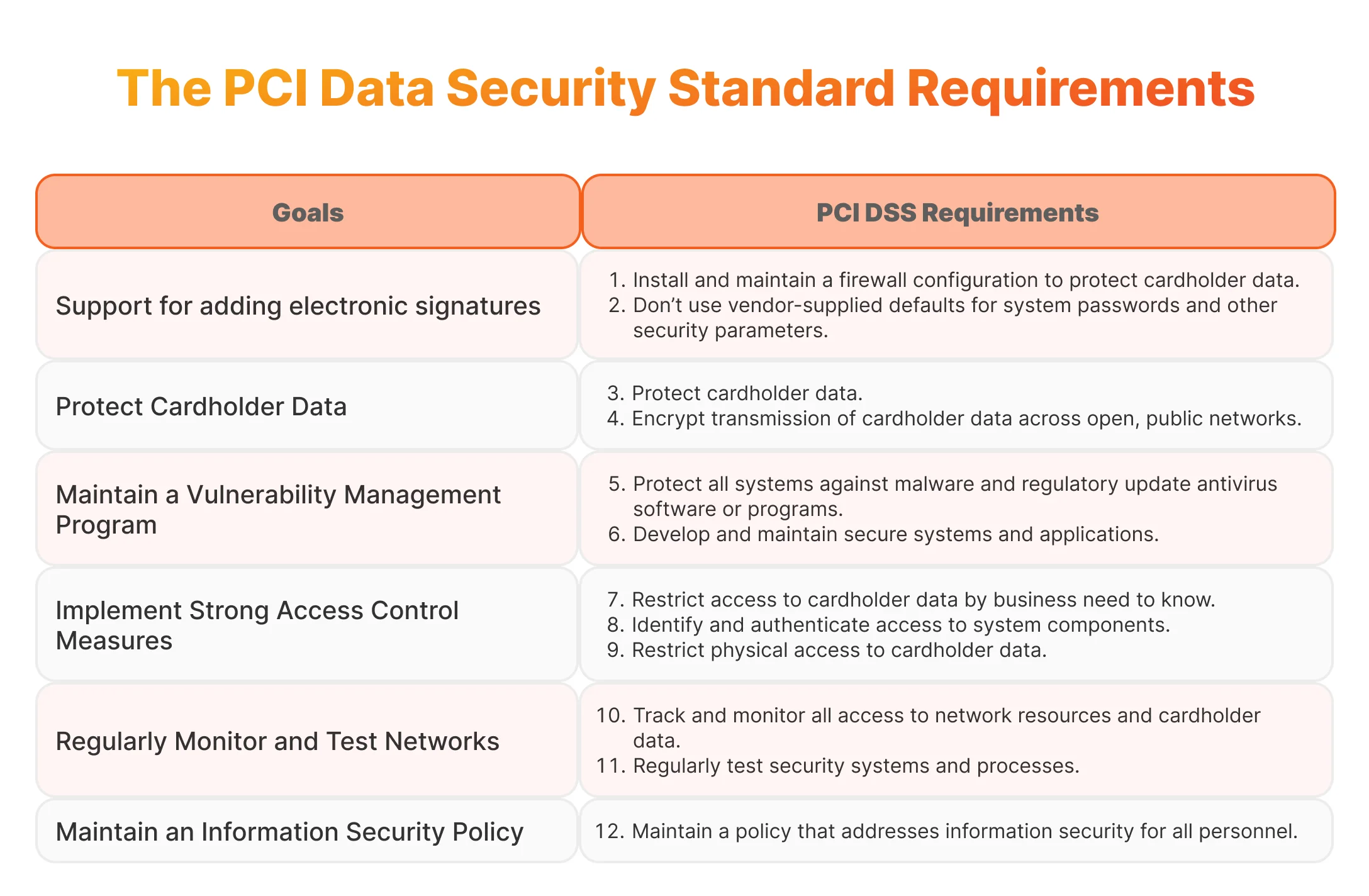
1. Build and Maintain a Secure Network
1.1 Requirement: Install and maintain a firewall configuration
This involves implementing specific security measures organizations should follow to safeguard cardholder data and comply with the standard’s requirements.
Tips for compliance:
- Identify and document all systems and components that store, process, or transmit cardholder data, including defining the scope and boundaries of the Cardholder Data Environment (CDE).
- Install firewalls at network perimeters and between different segments within the CDE to establish secure zones and control traffic between trusted and untrusted networks.
- Implement a default deny rule on firewalls to deny all incoming and outgoing traffic and only allow specific, necessary traffic through explicit rules.
- Implement network segmentation to isolate the CDE from other parts of the network.
- Use Access Control Lists (ACLs) to define and enforce network traffic policies, explicitly specifying which IP addresses, protocols, and ports are allowed or denied.
- Enable logging on firewalls and review firewall logs for suspicious activity or security incidents.
- Remove any unnecessary or outdated rules to reduce the attack surface.
- Document and review any changes to firewall rules to ensure they comply with the latest security policies and PCI DSS requirements.
- Consider inspecting and controlling traffic at the application layer.
- Conduct regular penetration testing to identify and address potential vulnerabilities in the firewall configuration.
1.2. Requirement: Do not use vendor-supplied defaults for system passwords and other security parameters
This can be a major problem in big organizations and systems with a high number of elements.
Tips for compliance:
- Immediately change all default usernames and passwords on systems, devices, and applications upon installation.
- Ensure that all system components and software have unique, complex, and strong passwords.
- Regularly update and rotate passwords.
- Scan systems using automated tools or scripts to identify and remediate any instances where default credentials may still be in use.
2. Protect Cardholder Data
2.1. Requirement: Protect stored cardholder data
The goal here is to secure sensitive information related to credit and debit card transactions to prevent unauthorized access and potential breaches.
Tips for compliance:
- Clearly define and identify what constitutes cardholder data within your organization.
- Implement access controls to restrict access to cardholder data on a need-to-know basis, ensuring that only authorized personnel can access sensitive information.
- Enable detailed logging for all systems that handle cardholder data.
- Implement secure storage practices for physical and electronic storage of cardholder data.
2.2. Requirement: Encrypt transmission of cardholder data across open, public networks
Transferring data over networks, especially public networks, puts sensitive data at risk, so there is a need to enhance the security of cardholder information.
Tips for compliance:
- Use strong encryption protocols such as TLS (preferably) or SSL to secure the transmission of cardholder data. PCI DSS explicitly recommends discontinuing the use of early versions of SSL due to exposed vulnerabilities.
- Configure servers and devices to use strong cipher suites that provide robust encryption.
- Keep encryption protocols and software up to date with the latest security patches.
3. Maintain a Vulnerability Management Program
3.1. Requirement: Use and regularly update antivirus software or programs
Malware, viruses, and other malicious software are evolving constantly, so you need to keep your finger on the pulse of the latest security updates to identify and mitigate new and emerging threats effectively.
Tips for compliance:
- Install antivirus software on all systems within the CDE, including servers, workstations, and any other devices that handle cardholder data.
- Ensure that endpoints, such as employee workstations, point-of-sale (POS) terminals, and servers, are protected by antivirus software.
- Configure antivirus software to receive regular updates to virus definitions and signatures.
- Enable automated updates whenever possible to ensure that antivirus protection is consistently up-to-date.
3.2. Requirement: Develop and maintain secure systems and applications
This requirement focuses on building and sustaining a secure environment for systems and applications that handle cardholder data.
Tips for compliance:
- Implement security considerations from the early stages of the Software Development Life Cycle (SDLC).
- Integrate security practices into requirements, design, coding, testing, and deployment phases.
- Perform thorough security testing, including static code analysis, Dynamic Application Security Testing (DAST), and penetration testing.
- Implement a robust patch management process to promptly apply security updates and patches.
- Regularly update software, operating systems, and third-party libraries to address known vulnerabilities.
- Conduct regular vulnerability assessments to identify and address potential weaknesses.
4. Implement Strong Access Control Measures
4.1. Requirement: Restrict access to cardholder data by business need-to-know
This requirement emphasizes the importance of limiting access to cardholder data to only those individuals who require it to perform their job responsibilities.
Tips for compliance:
- Clearly define roles and responsibilities within the organization that involve access to cardholder data.
- Document the specific business processes and legitimate reasons for accessing cardholder data for each role.
- Utilize Role-Based Access Control (RBAC) mechanisms to grant access permissions based on job roles.
- Regularly review access logs to detect and investigate any unauthorized or suspicious activities.
- Update access permissions to ensure alignment with current job roles.
4.2. Requirement: Assign a unique ID to each person with computer access
This requirement is designed to enhance security by ensuring that every individual who has access to computer systems and cardholder data has a unique and traceable identifier.
Tips for compliance:
- Assign a unique User Identifier (ID) to each person who has computer access within the organization.
- Use unique IDs with strong user authentication mechanisms, such as complex passwords, two-factor authentication, smart cards, or biometrics.
- Promptly deactivate or update a unique ID when an employee leaves the organization or changes roles.
4.3. Requirement: Restrict physical access to cardholder data
This requirement is aimed at ensuring the physical security of systems and devices that store, process, or transmit cardholder data. Restricting physical access helps prevent unauthorized individuals from physically compromising cardholder data, such as through theft or tampering.
Tips for compliance:
- Implement physical access control mechanisms to restrict access to areas containing cardholder data, including access control systems, key cards, biometric authentication, surveillance, visitor logs, and other security measures.
- Enforce escort policies for visitors to cardholder data areas, ensuring that they are accompanied by an authorized employee at all times.
- Incorporate procedures for responding to physical security incidents, such as unauthorized access or tampering with cardholder data.
- Regularly review and update access controls for physical areas where cardholder data is stored.
5. Regularly Monitor and Test Networks
5.1. Requirement: Track and monitor all access to network resources and cardholder data
This requirement is created to enhance the security of cardholder data by implementing robust logging and monitoring mechanisms.
Tips for compliance:
- Configure systems, applications, and network devices to generate detailed logs of relevant events. Logging should capture information about all access attempts, changes to configurations, and other security-relevant activities.
- Implement centralized logging where logs from various sources are aggregated into a central repository.
- Establish a schedule for regular reviews of log data and assign responsibility for log reviews to trained personnel or use automated tools to analyze logs.
5.2. Requirement: Regularly test security systems and processes
This requirement emphasizes the importance of conducting regular and comprehensive testing of security controls, processes, and systems to identify vulnerabilities, assess their effectiveness, and ensure ongoing compliance with PCI DSS.
Tips for compliance:
- Conduct regular vulnerability scans and penetration of systems within the CDE.
- Perform both internal and external vulnerability scans to identify weaknesses from both inside and outside the network perimeter.
- Conduct security assessments, which may include internal and external audits, to evaluate the effectiveness of security controls.
6. Maintain an Information Security Policy
6.1. Requirement: Establish, publish, maintain, and disseminate a security policy
This requirement is necessary to ensure that organizations have a documented framework for protecting cardholder data and maintaining a secure environment.
Tips for compliance:
- Align the security policy with relevant legal and regulatory requirements, including PCI DSS.
- Ensure that the security policy addresses the specific obligations and recommendations outlined in PCI DSS.
- Establish a process for regularly reviewing and updating the security policy.
- Update the policy to reflect changes in the organization’s infrastructure, technology, and regulatory landscape.
6.2. Requirement: Conduct regular security awareness training for all personnel
This requirement is for educating all individuals within an organization about security policies, procedures, and best practices to protect cardholder data.
Tips for compliance:
- Security awareness training should be provided to all personnel within the organization, including employees, contractors, and third-party vendors.
- Conduct security awareness training regularly, with a frequency that aligns with the organization’s policies and the dynamic nature of security threats. For example, recognizing and avoiding phishing attacks.
- Provide security awareness training as part of the onboarding process for new employees.
- Establish feedback mechanisms for employees to provide input on the effectiveness of training programs.
PCI DSS Compliance Checklist
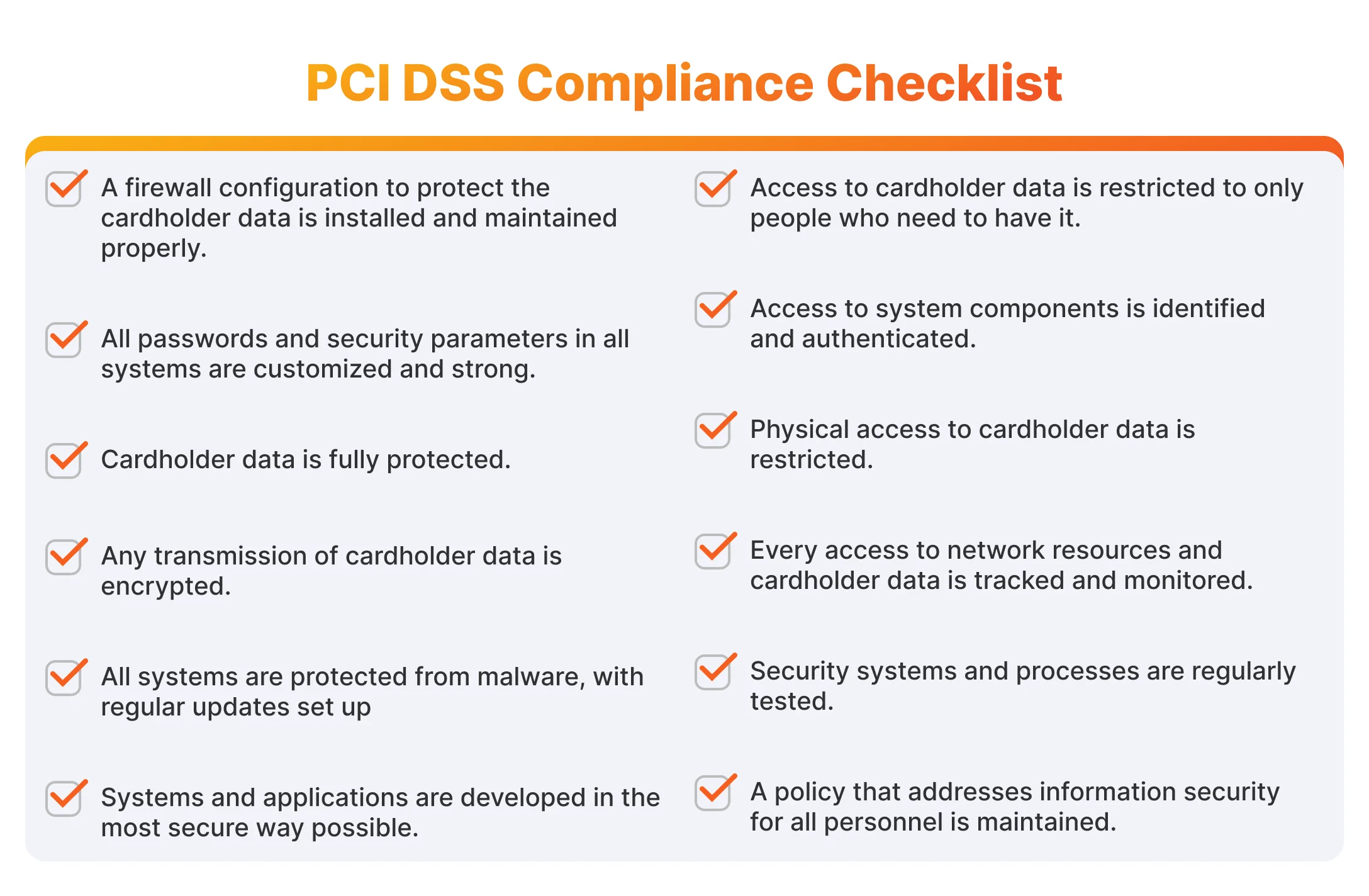
- A firewall configuration to protect the cardholder data is installed and maintained properly.
- All passwords and security parameters in all systems are customized and strong.
- Cardholder data is fully protected.
- Any transmission of cardholder data is encrypted.
- All systems are protected from malware, with regular updates set up.
- Systems and applications are developed in the most secure way possible.
- Access to cardholder data is restricted to only people who need to have it.
- Access to system components is identified and authenticated.
- Physical access to cardholder data is restricted.
- Every access to network resources and cardholder data is tracked and monitored.
- Security systems and processes are regularly tested.
- A policy that addresses information security for all personnel is maintained.
Conclusion
On average, it takes around 21 days to reach PCI DSS compliance, if you know how to do it right. We, at SPD Technology, have years of experience in building products in the Fintech industry, complying with any required standards and regulations. Feel free to contact us for help, and build a payment solution that will help you take the lead on your market!
FAQ
- What is a PCI compliance checklist?
It is a list of actions a company needs to take, to adhere to the Payment Card Industry Data Security Standard.
- How to ensure compliance with the PCI DSS checklist?
Your company needs to complete all twelve requirements for compliance, into six related groups known as control objectives:
1. Build and maintain a secure network and systems
2. Protect cardholder data
3. Maintain a vulnerability management program
4. Implement strong access-control measures
5. Regularly monitor and test networks
6. Maintain an information security policy.
